In a stunning admission, CISA reports that voting machines are vulnerable to tampering and hacking. After two-plus years of denials from multiple government officials, politicians, and the legacy media, the much delayed Cyber & Infrastructure Security Agency (CISA) report "identifie[d] vulnerabilities affecting versions of the Dominion Voting Systems Democracy Suite ImageCast X." The report warns the vulnerabilities present in the system software represent risks that "should be mitigated as soon as possible." CISA also reported that " it has no evidence that these vulnerabilities have been exploited in any elections." CISA Director Jen Easterly stated the same in a Tweet on Friday.
CISA has kept under wraps for almost a year a report from University of Michigan computer scientist J. Alex Halderman claiming the Dominion ImageCastX has vulnerabilities that could be exploited. The report was sealed by Federal Judge Amy Totenberg in the Curling v. Raffensperger case that has been ongoing since 2019.
According to ABC News, CISA argued:
"The document should not be made public until the agency has had time to assess and mitigate potential risks. The report has been under seal since July (of 2021) in federal court in Atlanta, part of a long-running lawsuit challenging Georgia's voting machines. Its author, J. Alex Halderman, said in sworn declarations filed publicly with the court that he examined the Dominion Voting Systems machines for 12 weeks and identified "multiple severe security flaws" that would allow bad actors to install malicious software."
According to the report, the following versions of the Dominion Voting Systems ImageCastX software are now known to be affected.
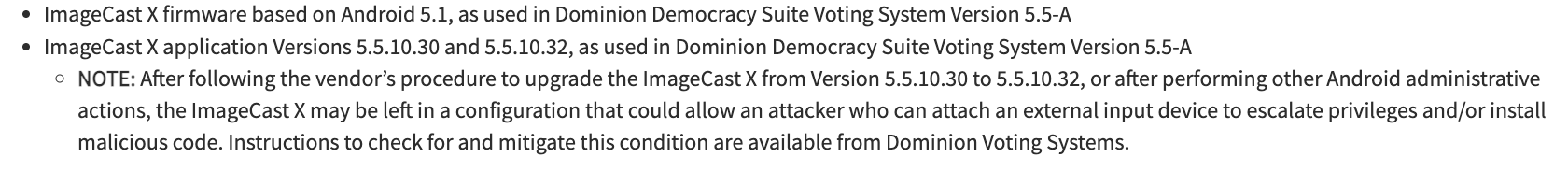 CISA Report/Affected Products
CISA Report/Affected Products
Notably, "other versions were not able to be tested." Drew Springall, who teamed up with Halderman, explains, "the vendor didn't give us or CISA access to test other versions."
The vulnerabilities are not insignificant. For example, CISA found "improper verification of cryptographic signature CWE-347." Application signatures must be validated to a "trusted root certificate." Processes that lack validation to the root certificate render the equipment vulnerable to undetected tampering. "An attacker could leverage this vulnerability to install malicious code," CISA reported, "Which could also be spread to other vulnerable ImageCast X devices via removable media."
The other listed vulnerabilities in the report are summarized as follows:
-
- Mutable attestation which could allow the "disguise of "malicious applications on a device."
- Hidden functionality—with the potential to give an "attacker" elevated privileges on a device.
- Improper protection of Alternate Path—which allows for rebooting in Android Safe Mode, allowing direct access to the operating system which could lead to escalation of privileges or the installation of malicious code.
- Path Traversal—or the ability to manipulate and cause arbitrary code execution, which could in turn "spread malicious code to ImageCastX devices from the Election Management System (EMS)."
- Execution with unnecessary privileges—allowing the execution of code to elevate privileges
- Authentication Bypass by Spoofing—making the machine vulnerable to forgery.
- Incorrect Privilege Assignment—with the potential to "expose cryptographic secrets used to protect election information—with the additional potential to affect other election equipment.
- Original Validation Error—this vulnerability makes the ImageCastX "susceptible to forgery," and an "attacker could leverage this vulnerability to print an arbitrary number of ballots without authorization."
CISA makes a number of recommendations in its advisory report to secure the votes of future elections when using electronic voting machines.
 CISA Mitigations/Electronic Voting
CISA Mitigations/Electronic Voting
However, because of the issues in 2020 and even in more recent primaries, many now believe that Americans should go back to paper ballots and hand counts—the way they used to be and how many countries continue to conduct their elections today including France. Halderman stated in a 2016 appearance on CSPAN that paper ballots can have their own set of issues; however, paper ballot technology is now available to address some of those concerns. "Paper technology is simple and is not terribly sexy," said Halderman, "But if it is done right, it provides a nice combination of a reliable record and security."
Right after the 2020 election, then-CISA Director Chris Krebs made the much-repeated statement at a Senate hearing to examine irregularities in the 2020 election that the "2020 Election was the most secure in U.S. history." Krebs said the same thing in a November 12, 2020, official joint statement from CISA. He was fired immediately by President Trump because of his statements. The irony is that Krebs also conceded in another official CISA statement on October 20, 2020, that voting "systems can malfunction, or could even be hacked."
UncoverDC has reported extensively on the 2020 election, including reports on the Dominion Voting Machine vulnerabilities. Mike Lindell has been at the forefront of investigating electronic voting systems, investing countless hours and millions of dollars attempting to prove voting machines are vulnerable to hacking and can be used to manipulate votes.
Notably, UncoverDC reported during the summer of 2021 that much of the market's voting equipment shares "DNA," meaning they share vulnerability "to the same gross security flaws."
"A total of five (5) companies conduct and administer elections for more than ninety percent (90%) of counties in the United States: (1) Election Systems & Software, (2) Dominion Voting Systems, (3) Smartmatic USA Corp., (4) Hart InterCivic, and (5) Tenex. "
Lindell's complaint alleges that all of the above providers' "electronic voting machines and election management systems are vulnerable to hacking, as has been published and presented to various congressional committees." It also contends that they all can be connected to the internet either directly or indirectly. It looks as though this has now been confirmed despite claims to the contrary from Dominion and others. Curiously, Dominion is a member of CISA's Election Infrastructure Sector Coordinating Council.
Alex Halderman was a key player in the Antrim County election fraud investigation. He performed a post-mortem analysis of the Antrim County 2020 election, releasing a report on March 26, 2021, where he recommended security improvements but found that most of the issues in that county were a "consequence of human errors...gaps in election procedures and their adherence." Antrim used ImageCastX in 2020. Starting on page 7 of his report, Halderman does a deep dive into the county's election technology, explaining how it works and what to look for to protect the integrity of elections.
Halderman has appeared on many media outlets over the years to explain tampering with voting machines "is easier than it should be." In the same aforementioned 2016 appearance, Halderman explains in great detail the work that needs to be done on "the critical infrastructure to ensure our voting technology is protected adequately." The interview features, at one point, Thomas Hicks, the Chair of the U.S. Election Assistance, stating emphatically that voting machines are in no way connected to the internet. Halderman says while the voting machines themselves are not connected to the internet, there is a way for data and "potentially malicious" software to get in and out of the devices indirectly through air-gapped connections and other means.


